1. With the evolution of borderless networks, which vegetable is now used to describe a defense-in-depth approach?
- Artichoke *
- Lettuce
- Onion
- Cabbage
2. What is a characteristic of a layered defense-in-depth security approach?
You are viewing: Which Aaa Component Can Be Established Using Token Cards
- Three or more devices are used.
- Routers are replaced with firewalls.
- When one device fails, another one takes over.
- One safeguard failure does not affect the effectiveness of other safeguards. *
3. Passwords, passphrases, and PINs are examples of which security term?
- Identification
- Authorization
- Authentication *
- Access
4. What is privilege escalation?
- Someone is given rights because she or he has received a promotion.
- Vulnerabilities in systems are exploited to grant higher levels of privilege than someone or some process should have. *
- A security problem occurs when high-ranking corporate officials demand rights to systems or files that they should not have.
- Everyone is given full rights by default to everything and rights are taken away only when someone abuses privileges.
5. What are two characteristics of the RADIUS protocol? (Choose two.)
- Encryption of the entire body of the packet
- The use of TCP port 49
- The use of UDP ports for authentication and accounting *
- Encryption of the password only *
- The separation of the authentication and authorization processes
6. Which component of AAA is used to determine which resources a user can access and which operations the user is allowed to perform?
- Auditing
- Accounting
- Authorization *
- Authentication
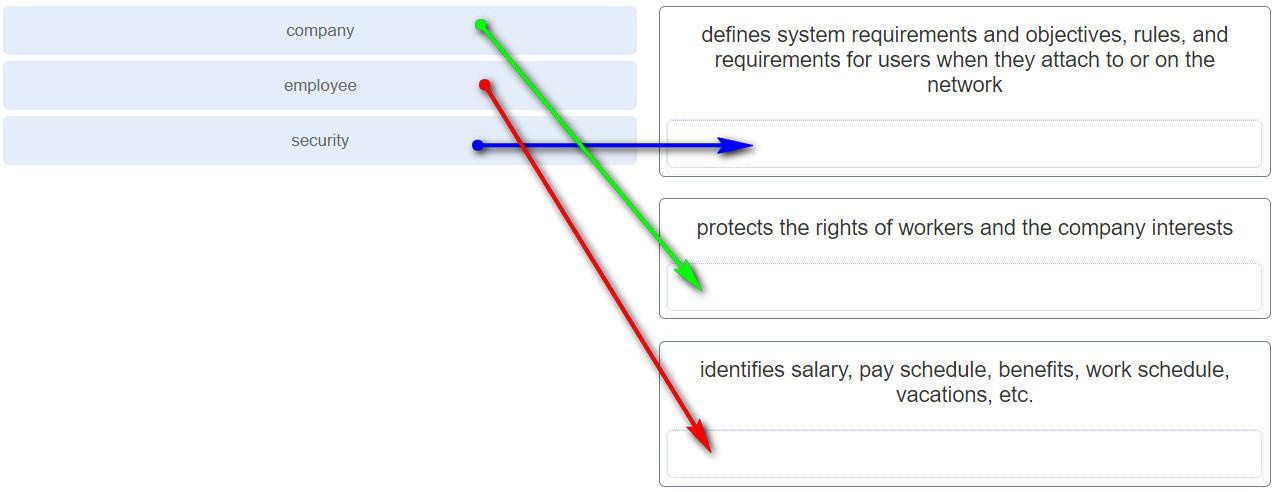
7. Which type of business policy establishes the rules of conduct and the responsibilities of employees and employers?
- Company *
- Data
- Employee
- Security
8. Which component of AAA allows an administrator to track individuals who access network resources and any changes that are made to those resources?
- Accessibility
- Accounting *
- Authentication
- Authorization
9. Which of the following offers a free service called Automated Indicator Sharing that enables the real-time exchange of cyberthreat indicators?
- FireEye
- Department of Homeland Security *
- The MITRE Corporation
- Talos
10. The security policy of an organization allows employees to connect to the office intranet from their homes. Which type of security policy is this?
- Acceptable use
- Incident handling
- Network maintenance
- Remote access *
11. During the AAA process, when will authorization be implemented?
- Immediately after successful authentication against an AAA data source *
- Immediately after AAA accounting and auditing receives detailed reports
- Immediately after an AAA client sends authentication information to a centralized server
- Immediately after the determination of which resources a user can access
12. A web server administrator is configuring access settings to require users to authenticate first before accessing certain web pages. Which requirement of information security is addressed through the configuration?
- availability
- confidentiality
- integrity
- scalability
Read more : Which Jojo Are You
13. What component of a security policy explicitly defines the type of traffic allowed on a network and what users are allowed and not allowed to do?
- password policies
- identification and authentication policies
- remote access policies
- acceptable use policies
14. What is the principle of least privilege access control model?
- User access to data is based on object attributes.
- Users are granted rights on an as-needed approach.
- Users are granted the strictest access control possible to data.
- Users control access to data they own.
15. Which statement describes a difference between RADIUS and TACACS+?
- RADIUS is supported by the Cisco Secure ACS software whereas TACACS+ is not.
- RADIUS encrypts only the password whereas TACACS+ encrypts all communication.
- RADIUS separates authentication and authorization whereas TACACS+ combines them as one process.
- RADIUS uses TCP whereas TACACS+ uses UDP.
16. What is the purpose of mobile device management (MDM) software?
- It is used to create a security policy.
- It is used to implement security policies, setting, and software configurations on mobile devices.
- It is used by threat actors to penetrate the system.
- It is used to identify potential mobile device vulnerabilities.
17. What service determines which resources a user can access along with the operations that a user can perform?
- authentication
- biometric
- authorization
- accounting
- token
18. A company has a file server that shares a folder named Public. The network security policy specifies that the Public folder is assigned Read-Only rights to anyone who can log into the server while the Edit rights are assigned only to the network admin group. Which component is addressed in the AAA network service framework?
- automation
- accounting
- authentication
- authorization
19. In threat intelligence communications, what set of specifications is for exchanging cyberthreat information between organizations?
- Trusted automated exchange of indicator information (TAXII)
- Structured threat information expression (STIX)
- Automated indicator sharing (AIS)
- Common vulnerabilities and exposures (CVE)
20. What three items are components of the CIA triad? (Choose three.)
- integrity
- availability
- confidentiality
- access
- scalability
- intervention
21. A company is experiencing overwhelming visits to a main web server. The IT department is developing a plan to add a couple more web servers for load balancing and redundancy. Which requirement of information security is addressed by implementing the plan?
- integrity
- scalability
- availability
- confidentiality
22. Which AAA component can be established using token cards?
- authorization
- authentication
- auditing
- accounting
23. Which method is used to make data unreadable to unauthorized users?
- Encrypt the data.
- Fragment the data.
- Add a checksum to the end of the data.
- Assign it a username and password.
24. Which two areas must an IT security person understand in order to identify vulnerabilities on a network? (Choose two.)
- number of systems on each network
- network baseline data
- data analysis trends
- hardware used by applications
- important applications used
Read more : Which Pfd Would Be Considered Readily Accessible
25. Which three services are provided by the AAA framework? (Choose three.)
- autoconfiguration
- automation
- authorization
- authentication
- accounting
- autobalancing
26. How does BYOD change the way in which businesses implement networks?
- BYOD provides flexibility in where and how users can access network resources.
- BYOD requires organizations to purchase laptops rather than desktops.
- BYOD users are responsible for their own network security, thus reducing the need for organizational security policies.
- BYOD devices are more expensive than devices that are purchased by an organization.
27. Which technology provides the framework to enable scalable access security?
- AutoSecure
- role-based CLI access
- authentication, authorization, and accounting
- Simple Network Management Protocol
- Cisco Configuration Professional communities
28. Which device is usually the first line of defense in a layered defense-in-depth approach?
- access layer switch
- internal router
- edge router
- firewall
29. Which type of access control applies the strictest access control and is commonly used in military or mission critical applications?
- mandatory access control (MAC)
- discretionary access control (DAC)
- attribute-based access control (ABAC)
- Non-discretionary access control
30. In a defense-in-depth approach, which three options must be identified to effectively defend a network against attacks? (Choose three.)
- assets that need protection
- location of attacker or attackers
- total number of devices that attach to the wired and wireless network
- threats to assets
- vulnerabilities in the system
- past security breaches
31. Which section of a security policy is used to specify that only authorized individuals should have access to enterprise data?
- statement of authority
- statement of scope
- campus access policy
- Internet access policy
- identification and authentication policy
- acceptable use policy
32. What device is usually the first line of defense in a layered defense-in-depth approach?
- Edge router
33. What component of a security policy explicitly defines the type of traffic allowed on a network and what users are allowed and not allowed to do?
- Acceptable use policies
34. Match the type of business policy to the description.
Answer
Source: https://t-tees.com
Category: WHICH